Introduction:
ADS (Alternate Data Streams) in NTFS Windows is a fascinating and lesser-known feature that provides a hidden dimension to file storage. In this blog post, we will embark on a journey to understand ADS, its significance, and the possibilities it offers. Get ready to delve into the world of hidden data and unlock the secrets that lie beneath the surface.
Exploring ADS:
We will begin by explaining what ADS is and how it functions within the NTFS file system. ADS allows files to have additional streams of data attached to them, which are often hidden from plain view. We will explore the purpose of ADS, its benefits, and the scenarios where it can be utilized effectively.
Understanding the Implications:
While ADS has its advantages, it also raises concerns related to security and privacy. We will discuss the potential risks associated with ADS and the precautions that need to be taken to ensure data integrity and protection.
Real-world Applications:
ADS finds practical applications in various fields. We will highlight some interesting use cases where ADS can be leveraged creatively, such as metadata storage, digital forensics, and data hiding techniques.
Working with ADS:
To provide a hands-on experience, we will walk through the process of working with ADS in NTFS Windows. From creating alternate data streams to accessing and manipulating the hidden data, we will cover the necessary steps and commands involved.
So, join us on this journey of exploration as we uncover the hidden world of ADS in NTFS Windows. Prepare to be amazed by the hidden treasures that await within your files.
Reading ADS:
Let's spouse I have a file in my home directory strangely named "hidden.txt".
I opened it and there is a message.

Okay So lets find out. To check for ADS (Alternate Data Streams) using cmd.exe
dir /R
It will list all ADS if available.

There is a datastream highlighted in the image above. Let's read it.
more < hidden.txt:showme
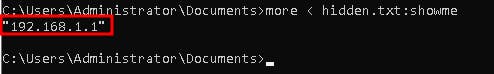
With this simple command in cmd. We can read hidden streams of any file in NTFS.
Now how do we create it?
Creating ADS:
To create ADS we just need the "echo" command.
echo "I am a secret!" > hidden.txt:secret
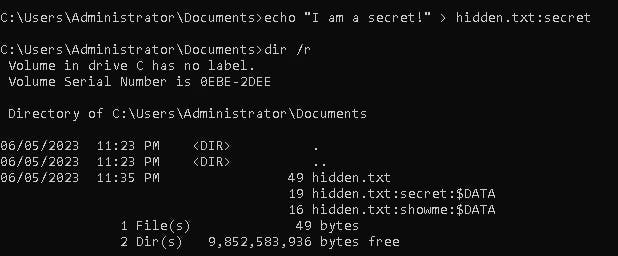
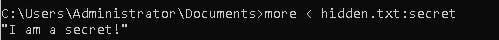
As we can see there is a second ADS named secret. Now we know the trick of how to read it.
more < hidden.txt:secret
Little Assignment:
Now here is the assignment for you. I want to research how to remove ADS. If you found that comment down below.
Q1: How to remove ADS in NTFS?
Conclusion:
ADS in NTFS Windows opens up a realm of hidden possibilities, allowing us to store additional data within files without altering their primary content. It is an intriguing feature that brings an extra layer of functionality and flexibility to file management. By understanding ADS, we can utilize its potential wisely while being mindful of the security aspects.

